
Overview
We continue building out our IoT Pi project with a small backtrack.
In a previous post, we created a cluster of Raspberry Pis using Kubernetes. Life with k8s was great until instability set in. It appeared that most of the issues were with the network driver Flannel. we experienced
- Lost/Unrecoverable nodes
- Kernel panics
- Network connectivity issues
We had hopes that the latest version would help with these issues but it appears we may never know as there is a bug preventing flannel from working with our Raspberry Pis.
Swarm to the Rescue
Current versions of Docker include swarm mode. Swarm mode is used for managing a cluster of docker engines called a swarm
Setup
Flash HypriotOS on your SD cards
You can find the latest release at HypriotOS. They also provide a pretty handy flash tool which you can use like:
|
1 2 3 |
flash --hostname pecan-pi https://github.com/hypriot/image-builder-rpi/releases/download/v1.5.0/hypriotos-rpi-v1.5.0.img.zip |
The --hostname enterprise is the name given to the Pi. You can also add other parameters. You can add WIFI information if you are using WIFI for your network. -s YOURSSID -p YourNetworkPassord.
After flashing the OS to the SD cards, install them in your Pi’s, boot them up and log in via SSH
|
1 2 3 |
ssh pirate@pecan-pi.local |
with a default password of hypriot
Living on the Bleeding Edge Always has Consequences
In Docker 1.13, a default iptables FORWARD policy was changed from ACCEPT to DROP (#28257). This change causes an issue with exposed services
If we run all our applications with the same docker network, this isn’t an issue but for testing purposes we need to find a workaround to hit services from the outside world. I am opting for creating a systemd service which simply modifies the iptable rules after docker has made its changes. When this issue is fixed, we can disable or remove the service.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
sudo cat << EOF |sudo tee /etc/systemd/system/k8s-iptables.service [Unit] Description=update iptables for k8s After=docker.service [Service] ExecStart=/sbin/iptables -P FORWARD ACCEPT Type=simple User=root [Install] WantedBy=multi-user.target EOF sudo systemctl enable k8s-iptables sudo systemctl start k8s-iptables |
Initialize the Swarm
|
1 2 3 |
$ docker swarm init --advertise-addr MANAGER-IP |
Running this on the master node will look like:
|
1 2 3 4 5 6 7 8 9 10 11 12 |
$ docker swarm init --advertise-addr 10.0.1.202 Swarm initialized: current node (nsnxs6oypgbsh24mvagifv8ro) is now a manager. To add a worker to this swarm, run the following command: docker swarm join \ --token SWMTKN-1-2ez1j9zvep9sz1owt7zgmb98s9785n1mvr83gcdty7v8k4c2x0-1w2yukwhkcfs6m1pyn3ff75gs \ 10.0.1.202:2377 To add a manager to this swarm, run 'docker swarm join-token manager' and follow the instructions. |
The --advertise-flag configures the manager node to publish its address as 10.0.1.202. The other nodes in the swarm must be able to access the manager at that IP address.
Running the join command on a worker nodes results in:
|
1 2 3 4 5 6 |
$ docker swarm join \ > --token SWMTKN-1-2ez1j9zvep9sz1owt7zgmb98s9785n1mvr83gcdty7v8k4c2x0-1w2yukwhkcfs6m1pyn3ff75gs \ > 10.0.1.202:2377 This node joined a swarm as a worker. |
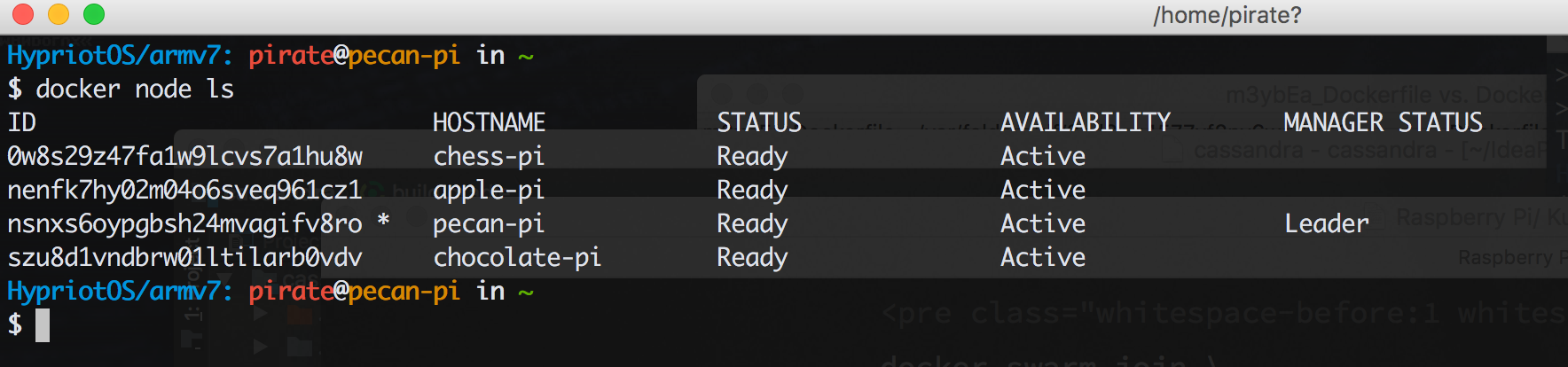
docker node ls on the master node will then show the state of the cluster


Social Media